Why the 'never trust, always verify' approach is becoming the standard for modern enterprise security.
The End of the Traditional Perimeter
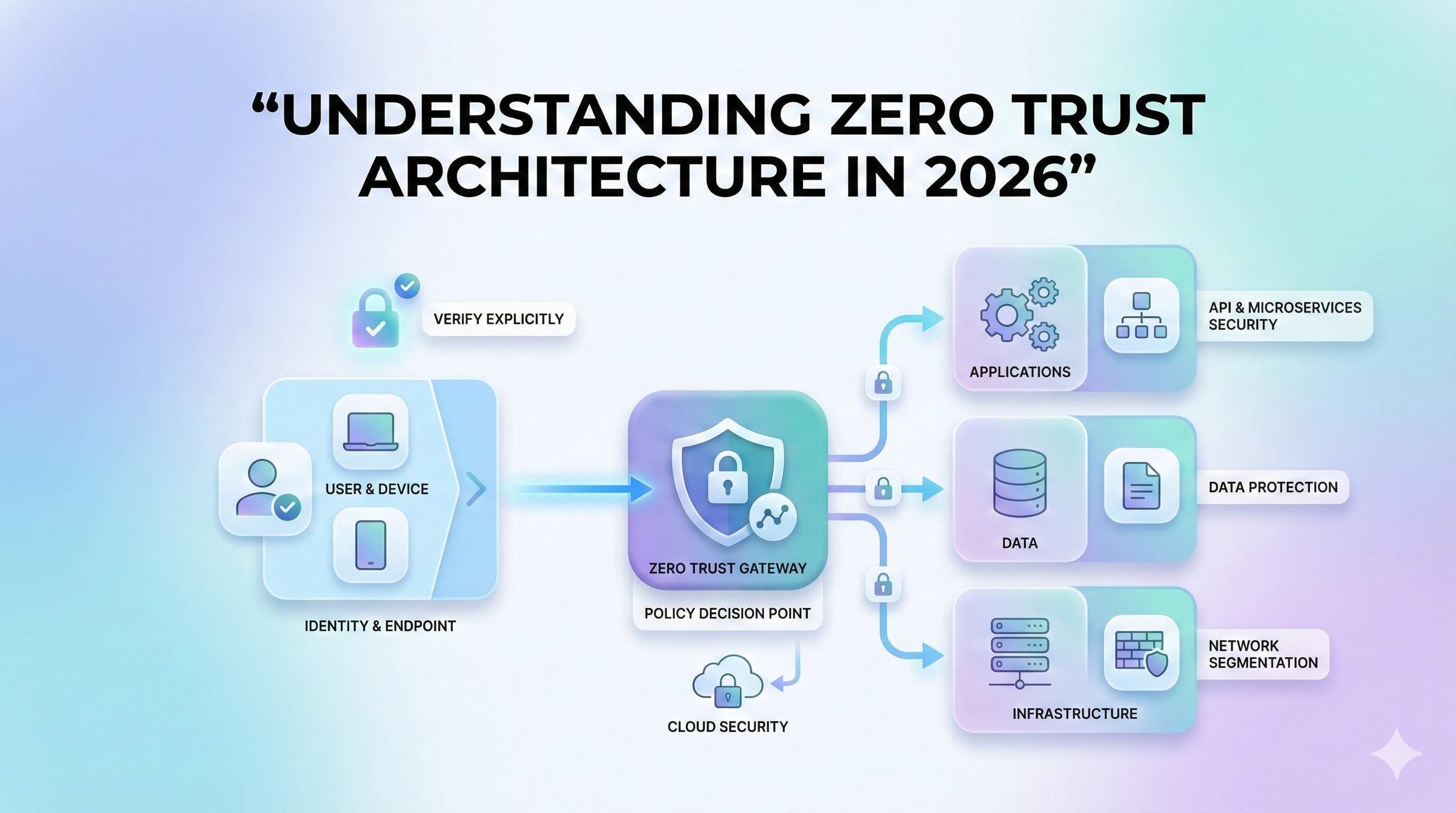
In the modern era of remote work and cloud-native applications, the traditional 'castle-and-moat' security model is no longer sufficient. Zero Trust assumes that threats could exist both outside and inside the network.
Core Principles
Zero Trust operates on three main pillars: explicit verification, least privilege access, and the assumption of a breach. Every access request is fully authenticated, authorized, and encrypted before granting access.
Implementing Micro-segmentation
By breaking down networks into smaller, isolated segments, organizations can prevent lateral movement by attackers, ensuring that a single compromised account doesn't lead to a total system breach.